The dark side of crypto innovation hides in plain sight, and crypto scam trackers reveal an alarming truth: fraudsters now deploy AI-powered cons, rug-pull algorithms, and deepfake “advisors” to exploit even savvy investors.
These digital predators evolve faster than security measures, turning blockchain’s transparency against users with military-grade precision. A crypto scam tracker is no longer optional armor—it’s your first alert when smart contracts turn predatory and “verified” projects vanish overnight.
This guide transforms you from target to threat hunter, teaching you how to weaponize tracking tools, decode malicious patterns, and build an early-warning system around your assets. In crypto’s Wild West, the best defense is a tracker-powered offense.
Common Types of Crypto Scams To Be Aware Of
As cryptocurrency adoption grows worldwide, so does the sophistication of scams targeting investors. Understanding these fraudulent schemes is your first line of defense.

By familiarizing yourself with common tactics and warning signs, you can develop the critical awareness to protect your digital assets from increasingly deceptive approaches.
- Rug Pulls:
These scams occur when developers abandon a cryptocurrency project after raising substantial investor funds. The team creates legitimate-seeming tokens and liquidity pools, attracts investment, and then suddenly “pulls the rug” by withdrawing all funds and disappearing, leaving investors with worthless tokens.
- Phishing Scams:
Fraudsters create convincing copies of legitimate crypto platforms or send deceptive emails directing users to counterfeit websites. Once victims input their credentials or private keys, scammers gain access to their wallets and drain funds. These attacks often exploit urgency, using security alerts or limited-time offers as bait.
- Pump-and-Dump Schemes:
Orchestrated price manipulations where scammers artificially inflate a cryptocurrency’s value through coordinated buying and false positive information, then sell their holdings once new investors drive the price up. When the orchestrators exit, prices collapse, leaving late investors significant losses.
- Fake ICOs/IDOs:
Fraudulent initial coin or decentralized exchange offerings present elaborate but ultimately hollow projects. They feature convincing whitepapers, fictional development teams, and aggressive marketing campaigns to collect investor funds before disappearing.
- Impersonation Scams:
Scammers pose as celebrities, crypto influencers, or project team members on social media, often creating nearly identical profiles. They typically promote giveaways requiring users to send cryptocurrency first, with promises of receiving double in return. Advanced versions may even employ AI-generated deepfakes for added credibility.
- High-Yield Investment Programs (HYIPs):
These modern Ponzi schemes promise unsustainable returns on crypto investments. Initial investors receive payments from new investor funds, creating the illusion of legitimacy until the scheme collapses when new investments dry up.
Red Flags to Watch For
Unrealistic Promises:
Any guarantee of specific returns in the volatile crypto market should immediately raise suspicion. Legitimate projects acknowledge risks rather than promising guaranteed profits.
Opaque Team Information:
Credible projects feature verifiable team members with established track records. Anonymous teams or those with unverifiable credentials indicate potential fraud.
Urgency Tactics:
“Limited-time” offers pressuring quick decisions without proper research are hallmarks of scams designed to bypass your critical thinking.
Poor Online Presence:
Unprofessional websites with spelling errors, inconsistent branding, or missing security features (like HTTPS) suggest fraudulent operations.
Private Key Requests:
No legitimate service will ever ask for your private keys or seed phrases. These requests always signal attempted theft.
Unusual Trading Patterns:
Sudden spikes in trading volume or price without corresponding news or developments often indicate manipulation rather than organic market activity.
What Are Crypto Scam Trackers?
With the increasing prevalence of cryptocurrency fraud, specialized tools have been developed to help investors navigate this complex landscape safely.
Crypto scam trackers represent a critical evolution in the community’s defense mechanisms, offering structured approaches to identifying and avoiding fraudulent schemes before they cause financial harm.
These are specialized databases that collect, organize, and make searchable information about known or suspected cryptocurrency scams.
These platforms compile data from multiple sources, including user-submitted complaints, regulatory actions, blockchain analysis, and community reports.
Most trackers allow users to search by:
- Company name
- Website URL
- Wallet address
- Scam type
Advanced versions may incorporate blockchain analytics to identify suspicious transaction patterns, while others rely more heavily on user reporting and verification processes.
How Does a Crypto Scam Tracker Help?
Crypto scam trackers provide essential protective tools in an increasingly complex digital asset landscape.
These specialized platforms offer multiple features that work together to help investors identify and avoid fraudulent schemes before they become victims.
- Real-time Updates: Quality trackers continuously add new scams as they’re detected, helping users avoid emerging threats before widespread damage occurs.
- Comprehensive Database: By maintaining detailed records of scam types, affected platforms, and victim experiences, trackers create a searchable knowledge base that improves collective security.
- User-friendly Interface: Effective trackers offer simple search functionality, allowing users to quickly verify the legitimacy of crypto projects or websites they’re considering.
- Alert Systems: Some trackers provide notification services warning users about new scams targeting specific cryptocurrencies or using particular techniques.
- Community Reporting: Many platforms include mechanisms for users to submit scam reports, creating a crowd-sourced early warning system that benefits the broader community.
- API Integration: Advanced trackers offer API access, allowing developers to incorporate scam detection into wallets, exchanges, and other cryptocurrency applications.
How To Use a Crypto Scam Tracker Effectively?
Knowing that crypto scam trackers exist is only the first step – learning to use them effectively is where their true value emerges.
The following guide will help you maximize the protective benefits of these tools, turning them from simple reference databases into active shields against potential fraud in your crypto journey.
The California Department of Financial Protection and Innovation (DFPI) Crypto Scam Tracker offers a powerful tool for identifying potential cryptocurrency fraud.
Here’s how to use it effectively:
Step 1: Access the tracker by visiting the DFPI website (dfpi.ca.gov) and reaching the Crypto Scam Tracker section under Consumer resources.
Step 2: Use the search bar to query by company or website name, scam type (e.g., “Pig Butchering” or “Fraudulent Trading Platform”), or keywords from complaint narratives.
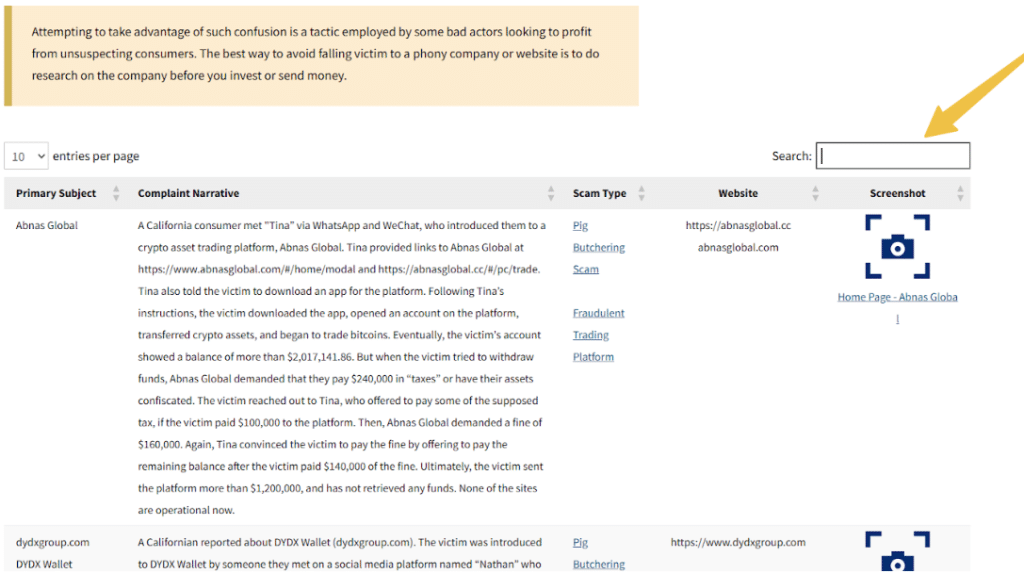
Step 3: Review complaint details, which include the primary subject (company or platform name), a detailed complaint narrative describing the scam, the categorized scam type, the website URL involved, and screenshots of the fraudulent platform (when available).

Step 4: Understand scam types by reviewing the comprehensive glossary below the tracker to understand various scam methodologies and their characteristics better.
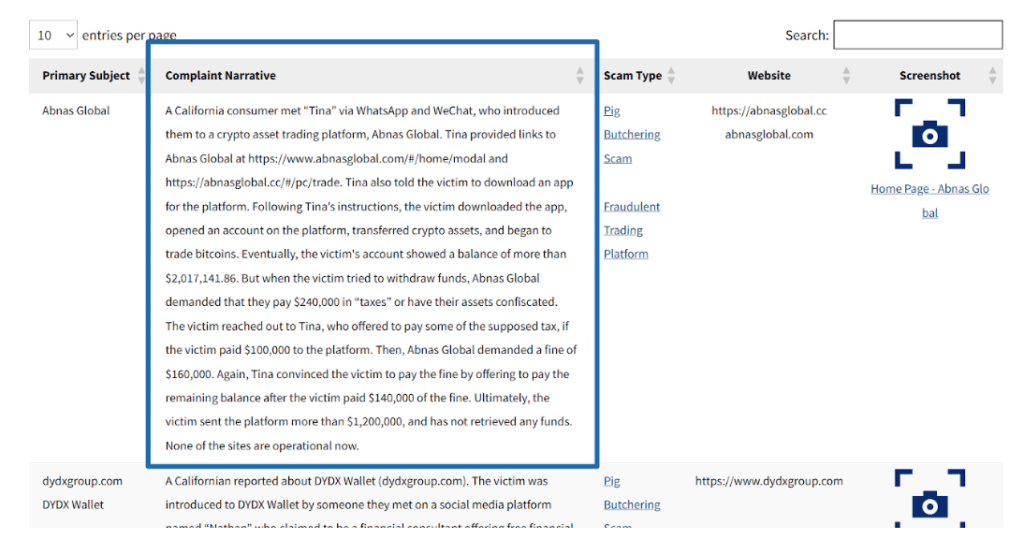
Step 5: Report new scams if you encounter a scam not listed in the tracker. To help protect others, submit a complaint through the DFPI online form or call their toll-free number (866-275-2677).
Step 6: Check imposter warnings by paying special attention to the “Note on Imposters” section highlighting how scammers create look-alike websites mimicking legitimate platforms.
How To Support Crypto Scam Tracker Data with Other Research?
While scam trackers provide valuable information, they should be one component of a broader due diligence strategy:
Cross-reference multiple sources: Check findings against other scam trackers, regulatory warnings, and community forums to establish consensus on potential threats.
Verify blockchain data: For suspicious projects, examine their smart contracts and token distribution using block explorers like Etherscan or BscScan to identify red flags in the underlying code or transaction patterns.
Community verification: Consult established cryptocurrency communities on platforms like Reddit, Discord, or specialized forums to gather additional perspectives on questionable projects.
Social proof investigation: Evaluate the project’s social media presence, checking for engagement authenticity, account age, and consistency across platforms.
Factors to Consider While Choosing the Right Crypto Scam Tracker
Not all crypto scam trackers offer the same level of protection or usability. Selecting the right tracker for your needs requires evaluating several key characteristics that determine how effectively the tool will serve as part of your security strategy.
The following considerations will help you identify trackers that provide reliable, actionable information.
- Accuracy and reliability:
The best trackers maintain strict verification processes for submitted reports and regularly update their databases to remove false positives. Look for trackers backed by reputable organizations with established expertise in cryptocurrency security.
- Frequency of updates:
Effective protection requires continuous monitoring of emerging threats. Quality trackers add new scams daily and modify existing entries as more information becomes available, rather than maintaining static databases.
- Ease of use:
The interface should allow intuitive navigation and quick verification of potential scams through simple searches. Complex systems with steep learning curves reduce effectiveness during time-sensitive decision-making.
- Cost structure:
While many quality trackers offer free basic access, premium features may require subscription fees. Evaluate whether additional capabilities like API access, custom alerts, or enhanced details justify the expense for your specific needs.
- Community engagement:
Trackers with active user communities often identify threats faster through crowd-sourced reporting. Look for platforms that balance community input with professional verification for optimal reliability.
- Institutional backing:
Trackers operated by government agencies, established security firms, or recognized blockchain organizations typically maintain higher standards for data quality and longevity of service.
Limitations of Crypto Scam Trackers
While crypto scam trackers provide valuable protection, understanding their inherent limitations is crucial for developing a comprehensive security strategy. No single tool offers a perfect defense against the evolving landscape of cryptocurrency fraud.
- Reporting Gaps: Most trackers rely on voluntary user reports, creating blind spots for unreported scams.
- Verification Challenges: Determining legitimacy often requires extensive investigation beyond user complaints.
- Adaptation Lag: The rapid evolution of scam techniques frequently outpaces tracking systems, as fraudsters continuously develop new approaches.
- Jurisdictional Complexity: Cross-border operations complicate enforcement efforts, with scammers operating across multiple jurisdictions to avoid consequences.
- Data Freshness Issues: Some trackers struggle with outdated information that may miss recent scams or falsely flag reformed platforms.
Users should approach trackers as helpful tools within a broader security framework rather than as complete protection solutions.
How To Stay Safe of Crypto Scams?
Beyond utilizing scam trackers, developing broader security awareness and practices is essential for long-term safety in cryptocurrency markets.
The following strategies complement tracker usage, creating multiple layers of protection against both known and emerging threats in this rapidly evolving ecosystem.
- Implement robust authentication:
Secure all cryptocurrency accounts with strong, unique passwords and hardware-based two-factor authentication like YubiKeys rather than SMS verification, which is vulnerable to SIM swapping attacks.
- Adopt cold storage solutions:
Store significant cryptocurrency holdings in hardware wallets disconnected from the internet, using online wallets only for active trading or smaller amounts needed for immediate use.
- Verify all communications:
Independently confirm messages claiming to be from exchanges or projects by visiting official websites directly rather than clicking links. Check for subtle URL differences that indicate phishing attempts.
- Maintain software hygiene:
Regularly update wallets, browsers, and security software to protect against known vulnerabilities. Use dedicated devices for high-value crypto transactions when possible.
- Practice transaction verification:
Double-check all wallet addresses before confirming transactions, using address whitelisting features when available on exchanges and wallets.
- Exercise skepticism toward unsolicited offers:
Legitimate crypto projects don’t need to approach you directly with investment opportunities. Treat unexpected contact with extreme caution, especially when promising returns or requesting information.
Staying Updated With Community
Cryptocurrency security benefits significantly from collective vigilance. When encountering suspicious projects or potential scams, share your findings through established channels:
- Report to relevant scam trackers to expand their databases
- Post detailed accounts in community forums like r/CryptoCurrency or project-specific Discord servers
- Alert regulatory authorities like the SEC, FTC, or DFPI
- Contact legitimate platforms being impersonated so they can warn their users
This collaborative approach strengthens the ecosystem’s immune system against fraud while providing educational opportunities for less experienced users.
Related Reads:
Conclusion: Use a Crypto Scam Tracker To Know & Report Crypto Scams
The crypto frontier demands a new breed of investor—one who wields crypto scam trackers like digital armor while mastering the art of defensive investing. These tools form your first alert system, but true security comes from layering them with blockchain literacy and community vigilance.
Remember that every reported scam strengthens the ecosystem’s defenses. As fraudsters refine AI-powered cons, your greatest weapon remains a simple habit—consulting your crypto scam tracker before every transaction.
The decentralized future belongs to those who trust, but verify. Stay skeptical, stay engaged, and let trackers transform you from potential victim to empowered participant in crypto’s evolution.
FAQs
Recovery is extremely difficult due to the irreversible nature of blockchain transactions. Report the scam immediately to law enforcement, exchanges, and authorities for the best chance of freezing funds before they’re moved.
Government trackers like California’s DFPI may take days or weeks due to verification processes, while community-driven platforms update more quickly but with varied reliability. Monitor multiple sources for maximum protection.
Scammers typically target popular cryptocurrencies like Bitcoin and Ethereum due to their wider user bases, while newer cryptocurrencies often face pump-and-dump schemes and rug pulls due to lower liquidity and scrutiny.
No tracker provides complete protection. Most identify website-based scams and reported addresses but struggle with sophisticated social engineering, real-time fraud, or private channel scams.
Evaluate the project’s transparency, technical fundamentals (audited smart contracts), community engagement, and realistic claims. Legitimate projects welcome scrutiny rather than pushing for quick investment decisions.
Absolutely. Reporting attempted scams provides valuable intelligence that helps protect others and contributes critical early warning data to the community’s collective security efforts.

![Top 15 Crypto Podcasts to Listen to in 2025 [Popular]](https://crypto.prosperityforamerica.org/wp-content/uploads/2025/03/Best-Podcasts-on-Cryptocurrency-1024x536.png)